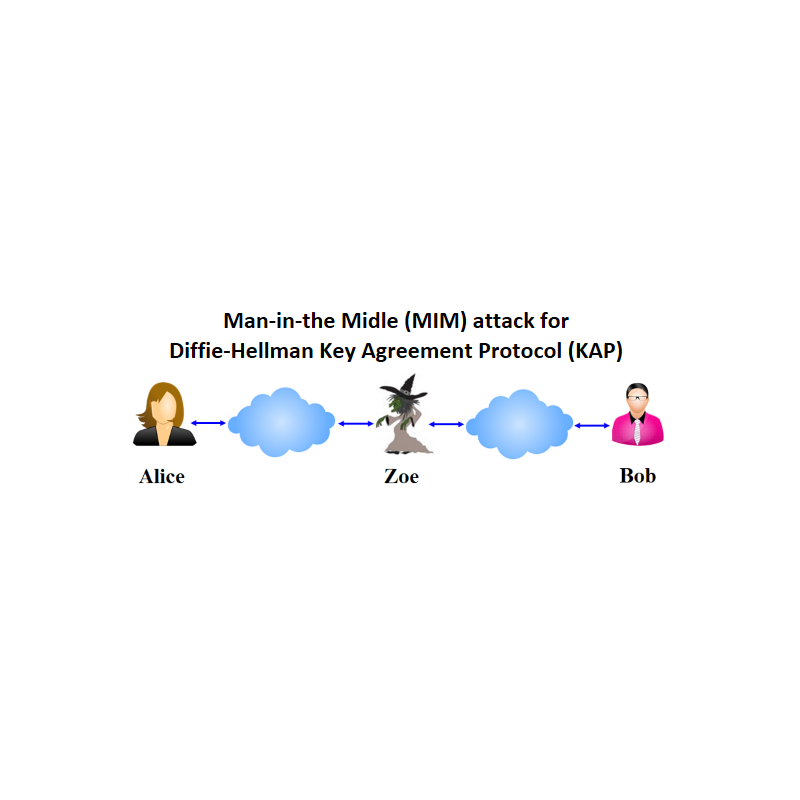


Man-in-the-Middle (MIM) attack to Diffie-Hellman (DH) Key Agreement Protocol (KAP).
Imagine You are an active adversary Zoe and want to arrange Man-in-the-Middle (MiM) attack to Diffie-Hellman (DH) Key Agreement Protocol (KAP) between Alice and Bob.
It is strongly recommended that you use Octave software implemented in your local computer rather than to use Octave in the server.
Public parameters (PP) known for all parties are strong prime number p=178096967 and generator g=20, where p is 28 bits length. Please check it for awareness.
Computed numerical parameter values sent by You (Zoe) must be included in the input field denoted by brackets [ ]. E.g., if you are impersonating Alice with computed parameter KZ1= 81905326, then symbolically in the input field you must enter [KZ1] which corresponds to enter 81905326 in the input field without brackets.
The following functions are used in the protocol:
>> mod_exp(g,x,p); % function computes modular exponent value gx mod p
>> randi(i); % i=26 – is recommended an upper range of generated random integer number